The steps or processes an enterprise follows during a cloud migration vary based on factors such as the type of migration it wants to perform and the specific resources it wants to move. That said, common elements of a cloud migration strategy include the following:
- evaluation of performance and security requirements;
- selection of a cloud provider;
- calculation of costs; and
- any reorganization deemed necessary.
At the same time, be prepared to address several common challenges during a cloud migration:
- interoperability;
- data and application portability;
- data integrity and security; and
- business continuity.
Without proper planning, a migration could degrade workload performance and lead to higher IT costs -- thereby negating some of the main benefits of cloud computing.
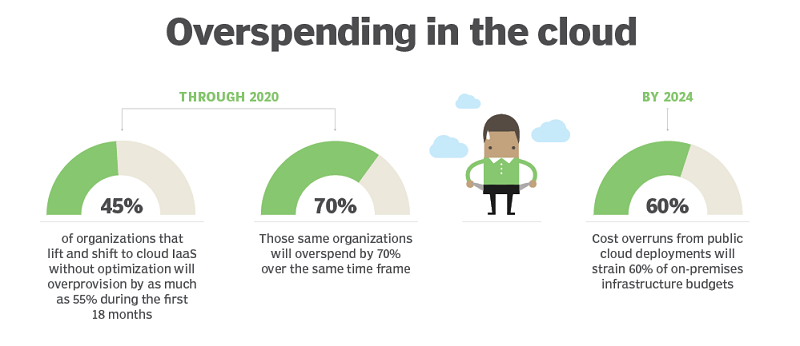
Don't overspend in cloud.
Depending on the details of the migration, an enterprise may choose to move an application to its new hosting environment without any modifications -- a model sometimes referred to as a lift-and-shift migration. In this scenario, a workload moves directly from local servers to the cloud without any changes. This is essentially a 1-to-1 move done primarily as a short-term fix to save on infrastructure costs.
In other cases, it might be more beneficial to change an application's code or architecture. This process is known as application refactoring or rearchitecting. It makes sense to refactor an application in advance of a cloud migration, but often it happens retroactively. This typically occurs once it is clear that a lift and shift has reduced an application's performance.
Refactoring an application can be costly, so IT management should consider whether this makes financial sense. Don't forget to calculate cost, performance and security when you analyze your ROI. It's likely that an application will require at least some refactoring, whether the transformation is minimal or comprehensive.
If a migration is done online, you will need to calculate how much bandwidth is necessary to make the move.
Enterprises have several choices when it comes to transferring data from a local data center to the public cloud. These include the use of the public internet or a private/dedicated network connection. Another option is an offline transfer, in which an organization uploads its local data onto an appliance and then physically ships that appliance to a public cloud provider, which then uploads the data to the cloud. The type of data migration an enterprise chooses -- online or offline -- depends on the amount and type of data it wants to move, as well as how fast it needs to complete the migration.
It might not be realistic to sideline your internet connection for lengthy periods of time. In some cases, it will make more sense simply to use a truck to transfer data instead of an internet connection. Physical shipment may not eliminate the need for additional syncing, but it can cut time and expense to move the data.
Before the workload moves to production, it should be stress tested and optimized to deliver acceptable performance. It's also important to test failure conditions as well as redundant systems.
Once the cloud migration is complete, staff will shift its focus to data performance, usage and stability. Be sure to budget for these tools, as they are often forgotten in the initial planning.
Here's where IT staff sees the biggest change in their support role. There is some reduction in overall hardware support. But cloud workloads must be managed, so it makes sense to add some cloud management training classes for the team. There may be some special considerations for the new security realities during a migration.
Ensuring application security in the cloud is always a concern, particularly during a live migration to the cloud. VM migrations are essential to balance a workload's need for compute, storage and other application demands.
Live migration through a network makes possible various types of attacks. An attacker can take a VM snapshot and create a VM in a different context than its original intent. Those stolen credentials can duplicate and steal the snapshot or install rootkits or other malware for additional access. Thrashing is a persistent denial-of-service attack in which hackers force repeated migrations and disrupt computing processes by consuming system resources.

